Encrypt data and important things for information security
The computer network is an open environment, Information posted to or received from the Internet may be exposed to objects. One of the most popular and secure methods of data security today is data encryption. However, Not everyone knows what data encryption is, How does it work and how does the encryption work?.
1. Mã hóa dữ liệu là gì?
Understandably, encryption is a method of protecting information, by converting the information from the normal readable and understandable form into the usual incomprehensible information that only the person who has access to the decryption key or password can read it. Doing this helps us to better protect information, Secure data transmission. In fact, data encryption will not prevent the data from being stolen, but it will prevent others from being able to read the contents of that file, because it has been turned into a different character form, or other content. The encrypted data is often called the ciphertext, common data, Unencrypted is called plaintext.
2. Vì sao việc mã hóa dữ liệu lại đặc biệt quan trọng?
The encryption is to ensure information security, especially in today's digital age. Especially in electronic transactions. It can be said that encryption is the secret guarantee , information integrity, when information is transmitted on the internet. Encryption is also the cornerstone of digital signature technology, PKI system
3. Chức năng chính của mã hóa dữ liệu
The purpose of data encryption is to protect digital data when it is stored on computer systems and transmitted via the Internet or other computer networks.. Cryptographic algorithms often provide key security elements such as authentication, Integrity and no withdrawal. Authentication allows verifying the source of data, Integrity proves that the content of the data has not been changed since it was sent. No revocation guarantees that people can't cancel sending data.
Encryption will turn the content into a new form, thus adding an extra layer of security to the data. So even if your data is stolen, deciphering the data is extremely difficult, consume a lot of computational resources and take a lot of time. With those companies, In organizations, the use of data encryption is essential. This will avoid damage when confidential information is accidentally exposed, It is also difficult to decode immediately.
Currently, many messaging applications use encryption to secure messages for users. We can mention Facebook, WhatApps with the type of encryption used is called End-to-End
4. Các phương pháp mã hóa
Data encryption is one of the most popular and effective data security methods, organized by many organizations, personal trust. Reality, Data encryption will not prevent data from being stolen, but it will prevent others from being able to read the contents of that file, because it has been turned into a different character form, or other content.
Classic coding
This is the oldest and simplest encryption method. Today this method is no longer used much compared to other methods. Because it's so simple. The idea of this method is: Party A encrypts the information using classical encryption algorithm, and Party B decodes the information, based on the algorithm provided by Party A, No need to use any key. So the full security of this type of encryption depends on the secrets of the algorithm. If a third person knows the algorithm, it is considered that the information is no longer confidential. Keeping the algorithm secret is extremely important, and not everyone can keep that secret completely.
One-way encryption (hash)
There are cases where we only need to encrypt information and not decode it. That's when we need to use this one-way encryption. For example, when you log into a website, Your password will be hashed (hash function) "chopped" , turned into a string of characters like "KhhdhujidbH". The essence, The database stores these encrypted characters and not your passwords. If a hacker steals data, he will only see cryptic characters and not know what your real password is.

The feature of the hash function is innermost 1 condition, If the input is the same, it will produce the same result. If only need to change one character in the string, from uppercase to lowercase, The result will be completely different. That is why people use the hash function to check the integrity of the data.
The current, The two most commonly used hash functions are MD5 and SHA. If you download a file from the Internet, you will sometimes see the words MD5 provided by the author. You will have to enter the code that appears as required. The purpose is for you to compare the downloaded file with the original file for errors.
Asymmetric encryption
This type of encryption is also known as public key encryption. It uses up to two keys (key) different. A key is called a public key (public key) and another key is the secret key (private key). Data is encrypted by public key. Everyone can get this key. However to decode the data, The recipient needs to have a private key.
To perform asymmetric encryption then:
– The recipient will generate a met key (public key và private key), they will retain the private key and pass it on to the sender of the public key. Because this public key is public, it can be freely transmitted without security.
– Before sending the message, The sender will encrypt the data using asymmetric encryption with keys received from the recipient
– The recipient decrypts the data received using the algorithm used on the sender, with decryption key as private key.
The biggest weakness of this type of encryption is very slow encoding and decoding. Using asymmetric encryption in data transfer is very costly and time consuming.
Common asymmetric encryption algorithm: RSA.
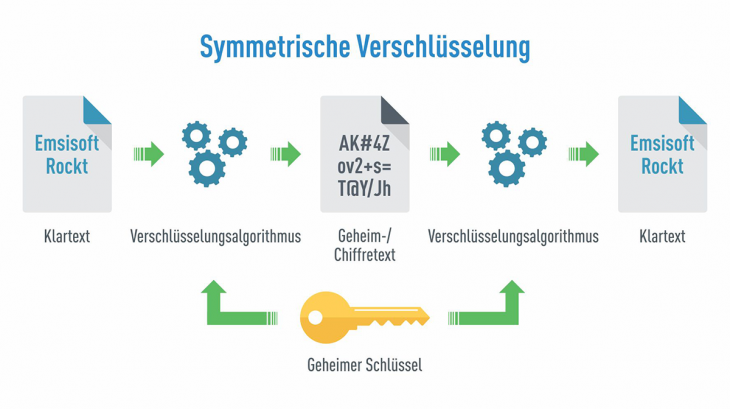
Symmetric encryption
This encryption method only needs the same key to encrypt and decode. According to some documents, symmetric encryption is the most commonly used solution today.

The coding process is described as follows:
-Use random coding algorithm + key to encrypt the data sent.
-By some way, The sender's key will be sent to the recipient, can be delivered before or after file encryption are okay.
-When the recipient receives data, they will use this key to decode data to get standard data.
However, the security issue lies in that, how to pass the key to the recipient safely. If this key is revealed, Anyone who uses the above algorithm can decrypt such data so the security will be no more.
We will often see two common algorithms are DES and AES. The DES algorithm has been around since year 1977 should not be commonly used by AES. AES algorithm can use different memory cell sizes to encrypt data, Commonly seen are 128-bit and 256-bit, There are some up to 512-bit and 1024-bit. The larger the memory cell size, the harder it is to break the code, In return, decoding and encryption also need more processing power.
Ứng dụng của mã hóa dữ liệu được áp dụng trong
♦ Database
In SQL Server you can create your own functions or use external DLLs to encrypt data like:
Encrypted by password
Symmetric key encryption
Asymmetric key encryption
Encryption certificate
♦ HTTPS protocol
HTTPS uses the TLS encryption algorithm (Hybrid between symmetrical and asymmetric) to encrypt your data when sending information between the browser and the server.
HTTPS is an encrypted form of information on the move, and people can use encryption to keep a lot of things safe, from email, mobile information, Bluetooth to application into ATMs.
♦ USB
USB today also comes with the included AES software so you can encrypt your data via a password, if you accidentally lose your USB, there's no need to worry about someone stealing the data contained inside. Even if the bad guy tries to remove the chip, attached to another piece of hardware to read only encoded data.
♦ Electronic signature
Digital signature is a form of electronic signature based on public key technology. Each user of a digital signature must have a key pair (keypair), including public key (public key) and secret key (private key). Secret key used to create digital signatures. The public key is used to verify the digital signature or authenticate the person who created that digital signature.
Một số cách mã hóa dữ liệu
Whatever you store data in any way, on USB, email or directly on your computer hard drive, You also need to set up more 1 or multiple layers of protection for files or folders for security.
And setting a password for a file or folder is the safest way to encrypt and protect data. Your file or directory will be encrypted and can only be opened or used by the password declaration.
1. Generate and encrypt data
Windows XP allows users to create ZIP files with passwords set for encryption. However, This feature is in Windows 7 has been removed. If you want to do this, Users must proceed with downloading and installing software from th vendor 3. There are many programs that create and encrypt data with a password, Most of them are provided for free, However, The writer recommends using 7-ZIP software
After downloading and installing, Readers can create compressed files right in the software interface or from a command in the right-click menu of Windows Explorer with password settings for encryption.. And the type of encryption you should choose here is the AES-256 standard. So, Anyone who wants to decompress must enter a password to unlock the file and use it.
2. Encrypt Office documents
Microsoft Office's Microsoft Office software packages also provide users with the ability to set passwords for text files and spreadsheets to encrypt and protect files..
And in the Office version 2007, Microsoft has switched to using the AES standard for file encryption to improve file security and safety.
Data is stored on an encrypted drive (encryption volume) cannot be read if the user does not provide the correct encryption key in one of the three forms of password (password) or the file contains the key (keyfile) or encryption key (encryption key). All data on the encrypted drive is encrypted (eg file name, are folder, content of each file, free space, metadata ...).
Data can be copied from an TrueCrypt encrypted drive to an unencrypted normal drive on Windows (and vice versa) normally there is no difference at all, including drag-and-drop operations.
3. Use TrueCrypt to encrypt partitions
TrueCrypt is released by the TrueCrypt Foundation. The advantages are completely free software, open source code, You can create an encrypted virtual drive or encrypt your entire hard disk (including the Windows installation drive).
TrueCrypt's setup and management mechanism is encrypting the drive on the go (on-the-fly encryption). This means that the data is automatically encrypted or decoded as soon as it is written to the hard disk or as soon as the data is uploaded without any user intervention..
Data is stored on an encrypted drive (encryption volume) cannot be read if the user does not provide the correct encryption key in one of the three forms of password (password) or the file contains the key (keyfile) or encryption key (encryption key). All data on the encrypted drive is encrypted (eg file name, are folder, content of each file, free space, metadata ...).
Data can be copied from an TrueCrypt encrypted drive to an unencrypted normal drive on Windows (and vice versa) normally there is no difference at all, including drag-and-drop operations.
4. Use the encryption feature provided in Windows
If you are using a professional version of Windows such as Professional or Enterprise edition, You will be provided by Windows 1 number of professional encryption features, except Home version.
Include 2 feature
BitLocker:
Allows users to encrypt the drive partition, including USB. In terms of features, BitLocker is built similar to TrueCrypt, So you can choose to use 1 in 2.
Encrypting File System (EFS):
Allow users to lock individual files. You can use this feature by right-clicking on the file and selecting ‘Properties > Click Advanced in the General tab '. A window popped up, tick the option ‘Encrypt contents to secure data’.
Now you have encrypted the file with your Windows account, So if you lose your account, You considered lost file permanently!. You should also note that the file is only stored on the current hard drive, If you emailed, The security of the file will not be guaranteed or will be damaged.
Mã hóa dữ liệu trong hội nghị truyền hình
With the advent of Internet-based communication services, Data leak protection is a very important part. So, Encryption-enabled applications are one of the safest options for workstations that don't want to face the possibility of unauthorized access to information traffic., eg:
Steal your account and password;
Unauthorized recording;
Listen or follow the conference.
SSL encryption
SSL (Secure Sockets Layer) is an encryption protocol that provides secure communications and prevents tampering. SSL involves exchanging keys between 2 point: workstations and servers, in which they "agree" on how algorithms and keys encrypt information.
Hoạt động của mã hóa dữ liệu trong hội nghị truyền hình?
The use of SSL for video conferencing uses secure channels with unique symmetric encryption. for users to connect securely to the server, A process authentication key is sent from the server to the workstation. Exchange, The workstation receives this key, Then confirm the reliability of the source. Such a procedure for obtaining and agreeing is called a "handshake" or "SSL compliant procedure" between the server and the bridge and it continues throughout the videoconferencing., thus providing a safe and secure connection.
The main purpose of exchanging encryption and decryption keys is to create a secret workstation environment, known by server and workstation. Therefore unauthorized access will not be able to connect to the conference if it does not have a secret key.
The symmetric encryption AES standard is the most popular and the safest. Have 3 standard: AES-128, AES-192, AES-256. The difference between them is in the key, determined by the number of bits. The more bits the better level of security is provided with this key.
Therefore AES-256 is the most reliable key in 3 type on.
Source “internet”


